
Top 20 Cybersecurity Interview Questions and Answers
In today’s digitally driven world, cybersecurity, the practice of ensuring the confidentiality, integrity, and availability of digital information, has become a paramount concern for individuals and organizations alike. The ever-increasing reliance on interconnected technologies means that safeguarding data and systems is a necessity.
Cybersecurity professionals are the unsung heroes, standing as the last line of defense against an ever-growing spectrum of cyber threats. Their expertise, knowledge, and readiness are instrumental in protecting our most valuable assets – data, privacy, and the very foundations of our interconnected world.
This post, “Top 20 Cybersecurity Interview Questions and Answers,” serves not only as a resource for those embarking on careers in the field but as a reminder of the profound significance of cybersecurity in our modern age as it highlights the fundamental questions you might encounter in a cybersecurity interview, providing comprehensive answers to help you prepare and thrive in this ever-evolving and vital domain.
1. What’s the Difference Between Symmetric and Asymmetric Encryption?
Explanation of the question
Symmetric Encryption involves a single key for both encryption and decryption. Think of it like a traditional lock and key, where the same key (or password) is used to lock and unlock a door. This means that both the sender and receiver need to have the same key to encrypt and decrypt messages. It’s a relatively fast and efficient method, which makes it suitable for securing data at rest.
Asymmetric Encryption, on the other hand, uses a pair of keys: a public key for encryption and a private key for decryption. It’s like having a special lock where anyone can drop a message into a box (using the public key), but only the person with the corresponding private key can open and read it. This method is excellent for secure data transmission because the public key can be openly shared, while the private key remains a closely guarded secret.
Practical Example
Imagine Alice wants to send a secure message to Bob. If they use symmetric encryption, they both need to have the same shared secret key. But with asymmetric encryption, Bob can freely share his public key with anyone, and only he can decrypt the messages encrypted with his private key.
In summary, the main difference lies in the use of one shared key (symmetric) versus a pair of keys (asymmetric). Symmetric encryption is like a single key for a single lock, while asymmetric encryption is like a lock with two unique keys, one for locking and one for unlocking.
2. What Is SSL and Why Is It Not Enough When It Comes to Encryption?
Explanation of the question
SSL, which stands for Secure Sockets Layer, is a cryptographic protocol designed to provide secure communication over the internet. It’s primarily used to secure data transmission between a user’s web browser and a website’s server. SSL has been a cornerstone of online security for many years, ensuring that data, such as login credentials, credit card information, and personal details, remains confidential and tamper-proof during transit. It’s often symbolized by the padlock icon in your web browser’s address bar.
While SSL is a crucial component of online security, it’s essential to understand that it has limitations. It primarily secures the connection between your device and a web server by encrypting the data in transit. However, it doesn’t provide end-to-end encryption, meaning that the data could still be exposed at various points along its journey.
The encryption provided by SSL doesn’t protect your data once it reaches the server. It’s like sending a sealed letter that remains secure while in transit but can be opened and read by the recipient. This means that, if a malicious actor gains access to the server or if there are vulnerabilities in the website’s security, your data could be at risk.
Practical Example
Imagine you’re sending a confidential email via a web-based email service that uses SSL. The email is securely transmitted from your computer to the email server using SSL encryption. However, once it reaches the email server, it may be stored in an unencrypted form. If the server is compromised, the content of your email could potentially be accessed. So, while SSL is a critical part of online security, it’s not enough to guarantee the complete protection of your data. For comprehensive security, it’s essential to use additional measures like end-to-end encryption or secure storage practices to safeguard your information from all potential threats.
3. What Is Encryption, and Why Is It Important in Cybersecurity?
Explanation of the question
Encryption is a critical concept in the realm of cybersecurity. It involves the process of converting information or data into a code to prevent unauthorized access or reading. This conversion is done using encryption algorithms, which rely on mathematical functions to scramble the information. Essentially, encryption ensures that even if an unauthorized person gains access to the data, they won’t be able to make sense of it without the decryption key.
When addressing the importance of encryption in cybersecurity, it’s essential to highlight the following key points:
- Encryption safeguards sensitive data, such as personal information, financial details, and confidential business records, from unauthorized access. Even if a hacker breaches a network, they will only find encrypted data that is virtually impossible to decipher without the decryption key.
- Encryption ensures that personal communication, whether through emails, messaging apps, or online transactions, remains private. It prevents eavesdropping and cybercriminals from intercepting and understanding the content.
- Various regulations, such as GDPR and HIPAA, require organizations to protect sensitive data using encryption. Compliance with these regulations is vital for avoiding legal issues and maintaining a trustworthy reputation.
- Encryption not only protects data from unauthorized access but also safeguards it from tampering. If someone attempts to alter encrypted data, it will be rendered useless without the decryption key.
- In a world where data travels across networks and the internet, encryption ensures that information remains secure during transmission. It safeguards data from potential interception and manipulation.
- Passwords are often stored in encrypted forms to prevent hackers from easily obtaining and using them.
4. Explain the Concept of “Defense in Depth.”
Explanation of the question
“Defense in depth” is a cybersecurity strategy that involves layering multiple security measures to protect an organization’s assets. These layers include physical security, network security, access controls, intrusion detection, encryption, and more. If one layer is breached, there are still other safeguards in place to defend against threats, making it more challenging for attackers to compromise the system.
“Defense in depth” is a fundamental cybersecurity strategy used to protect computer systems and data from a variety of threats. It involves implementing multiple layers of security controls to create a robust defense system. Understanding this concept is crucial for anyone concerned about safeguarding digital assets.
Practical Example
To illustrate “defense in depth,” consider a corporate network. The outermost layer of defense might involve a firewall at the network perimeter to prevent unauthorized access. Beyond that, there may be intrusion detection systems and intrusion prevention systems that monitor for suspicious activity within the network. Within the network, data might be encrypted to protect it from eavesdropping. Additionally, role-based access controls restrict employees’ access to only the resources necessary for their job functions.
5. What Is a DDoS Attack, and How Does It Work?
Explanation of the question
A DDoS (Distributed Denial of Service) attack aims to overwhelm a target server, service, or network by flooding it with an excessive amount of traffic. Attackers use a network of compromised devices, often referred to as a botnet, to generate traffic. This surge in traffic disrupts the targeted system’s normal functioning, rendering it unavailable to legitimate users. DDoS attacks can exhaust resources like bandwidth, processing power, or memory, causing downtime and service interruptions.
Practical Example
To illustrate, consider a popular e-commerce website during the holiday shopping season. Attackers may launch a DDoS assault against the site, flooding it with traffic and rendering it inaccessible to genuine customers. As a result, the business experiences substantial financial losses, tarnishes its reputation, and struggles to recover.
6. Define the Process of Salting. What Is the Use of Salting?
Explanation of the question
Salting is a fundamental concept in the realm of data security, particularly in the context of password storage. It involves adding a random or pseudo-random value to a user’s password before hashing it. This additional value, known as the “salt,” serves to enhance the security of stored passwords.
Here’s how the process of salting works and its uses: –
Process
- When a user creates an account or changes their password, a random and unique salt is generated.
- The salt is then combined with the user’s password, creating a new string. For example, if the salt is “S3cr3tS@lt,” and the password is “MyPassword”, the combined string would be “S3cr3tS@ltMyPassword.”
- This combined string is then subjected to a cryptographic hash function. The hash function transforms the salted password into a fixed-length string of characters unique to that input.
- The resulting hash, along with the salt, is stored in the system’s database.
Use
- Salting significantly increases the security of stored passwords. Without salting, if two users have the same password, they will generate the same hash. However, with the use of salts, identical passwords will produce different hashes due to the unique salt for each user.
- Attackers often use precomputed tables called “rainbow tables” to crack hashed passwords. With salted passwords, every user’s password will have a unique salt, making these tables ineffective.
- Salting makes it computationally intensive and time-consuming for attackers to crack passwords through techniques like brute force or dictionary attacks. This buys time for system administrators to detect and respond to attacks.
- Even if a database breach occurs, the salted passwords are not directly usable by attackers. They would need to compute the hashes for each unique salt and password combination, which is a formidable task.
Practical Example
Consider a scenario where a website stores user password. To enhance security, the website’s database administrator implements salting. For each user, a unique random string, known as the salt, is generated and combined with the user’s chosen password. This combined value is then hashed and stored in the database.
For instance, if a user’s password is “Password123,” and their unique salt is “X7G9L,” the salted password might look like “X7G9LPassword123.” When the user attempts to log in, the system retrieves the stored salted password, adds the salt to the provided password, hashes the result, and checks it against the stored value. This additional layer of complexity makes it significantly more challenging for attackers to crack passwords, even if they gain access to the database.
7. How Does a Virtual Private Network (VPN) Enhance Security?
Explanation of the question
A VPN is a technology that establishes a secure, encrypted connection over a public network, typically the internet. It creates a virtual tunnel through which data can be transmitted securely. This encryption ensures that even if data is intercepted by malicious actors, it remains unreadable.
A VPN is employed for various purposes, including safeguarding sensitive information, anonymizing internet activity, and accessing restricted content. To understand how a VPN enhances security, one must explore the underlying mechanisms and applications that make it a valuable tool in the realm of digital security.
Practical Example
Consider a scenario where employees working remotely need secure access to the company’s internal network. A VPN can be used to create a secure connection, allowing employees to access sensitive company resources while maintaining data confidentiality. This ensures that even when working from unsecured public networks, the organization’s data remains protected.
8. Here’s How a VPN Enhances Security.
Explanation of the question
When you connect to the internet through a VPN, your data is encrypted. This means that any data transmitted, whether it’s personal messages, financial transactions, or sensitive business information, becomes virtually unreadable to anyone trying to intercept it. It’s like placing your data in a secure, impenetrable envelope before sending it across the digital highway.
A VPN creates a secure “tunnel” for your data to travel through. This tunnel prevents third parties, such as hackers, cybercriminals, or even your Internet Service Provider (ISP), from monitoring or intercepting your online activities. It’s like having a private, dedicated lane on the digital freeway.
A VPN can hide your IP address by routing your connection through servers located in different regions or countries. This makes it challenging for websites, advertisers, or malicious entities to track your online behavior or pinpoint your physical location.
When you connect to public Wi-Fi networks in cafes, airports, or hotels, you expose yourself to potential security risks. Hackers often target these networks to intercept data. A VPN shields your connection, making it extremely difficult for cybercriminals to eavesdrop on your activities, enhancing security while you’re on the go.
A VPN allows you to access content and websites that may be geographically restricted. This is especially beneficial for travelers and those living in regions where certain online services are limited. By encrypting your connection and routing it through servers in other locations, a VPN grants you access to a broader digital world.
Practical Example
Imagine you’re sitting in a coffee shop, using the public Wi-Fi network to access your bank account and make financial transactions. Without a VPN, your sensitive financial information—such as login credentials and account details—is transmitted over the open network, making it vulnerable to potential eavesdropping or hacking attempts by cybercriminals. However, if you activate a VPN on your device, it establishes a secure connection to a remote server. All your data is encrypted, and your real IP address is concealed. This ensures that your financial transactions are conducted within a secure, private, and anonymous environment.
9. What Countermeasures Will You Take to Secure a Server?
Explanation of the question
Securing a server is a critical task, and it involves implementing a combination of security measures to safeguard the system from various threats and vulnerabilities.
Enhance Server Security with 5 Key Defensive Measures:
Bolster Network Security
Strengthen your network’s defenses with robust firewalls and stringent access controls, allowing entry only to authorized users.
Robust Security Practices
Regularly audit server logs and configurations to identify vulnerabilities and detect unusual activities. Implement strict physical access controls for authorized personnel and enforce comprehensive security policies for server management and usage.
Stay Current and Backup Regularly
Keep your server’s software, operating system, and applications up to date with the latest security patches. Regular data backups are essential to guard against data loss and the threat of ransomware attacks.
Data Security via Encryption and Password Policies
Enhance data security by encrypting information during both transmission and storage. Implement and regularly update strong password policies and consider the use of two-factor authentication.
Intrusion Detection System (IDS)
Deploy an Intrusion Detection System (IDS) to identify and respond to any suspicious activities promptly.
10. Check Out the List of Passwords Below, Which Are Pulled Out From a Database and Choose the Passwords That Are in Line With the UCSC’s Password Requirements:
A. Password1
B. @#$)*&^%
C. UcSc4Evr!
D. akHGksmLN
Choose the passwords that are in line with the UCSC’s password requirements.
Explanation of the question
The answer is C (UcSc4Evr!). As per the UCSC requirements, password must:
- Be a minimum of 8 characters long.
- Include characters from at least three of these four categories: lowercase letters, uppercase letters, numbers, and special characters.
11. How Do You Prevent Identity Theft?
Explanation of the question
Being vigilant and proactive is crucial in safeguarding your identity in an increasingly digital world. Here are several proactive steps and measures to prevent identity theft:
- Stay informed about the latest identity theft techniques and scams. Awareness is your first line of defense.
- Enable 2FA as it adds an extra layer of security by requiring you to provide a secondary form of verification, such as a code sent to your mobile device, in addition to your password.
- Review your bank and credit card statements regularly for any unauthorized transactions.
- Ensure your home Wi-Fi network is password-protected and uses encryption. Avoid using public Wi-Fi networks for sensitive transactions, as they are more vulnerable to hacking.
- Be cautious about unsolicited emails, messages, or phone calls. Don’t click on links or download attachments from unknown sources. Verify the legitimacy of requests for personal or financial information.
- Safeguard your personal information like your Social Security number, driver’s license, or passport. Shred important documents before disposing of them.
- Consider using identity theft protection services that can monitor your personal information and alert you to suspicious activities.
- Adjust your social media privacy settings to limit the amount of personal information visible to the public.
12. Who Are White Hat, Grey Hat, and Black Hat Hackers?
White hat hackers, also known as ethical hackers, are individuals who use their hacking skills for legitimate and legal purposes. They are often hired by organizations to test their systems and find vulnerabilities before malicious hackers can exploit them. White hat hackers help improve security and protect against cyber threats.
Grey hat hackers fall between the ethical and unethical spectrum. They may break into systems without permission but not for personal gain or to cause harm. Instead, they aim to expose vulnerabilities and may inform the affected organization after compromising its security.
Black hat hackers are the malicious actors who engage in hacking for personal gain, financial profit, or causing harm. They exploit security vulnerabilities to steal data, conduct cyberattacks, and engage in other illegal activities.
13. What Is a Traceroute? Mention Its Uses.
Explanation of the question
Traceroute is a network diagnostic tool that helps identify the route and measure the transit delays of data packets across an IP network. It works by sending packets with an increasingly larger Time to Live (TTL) value and noting the intermediate routers’ responses.
Traceroute is commonly used for the following purposes:
- It helps identify network issues, such as high latency or packet loss, by revealing the path data takes and pinpointing problematic routers.
- It can expose the network path to a target server, aiding security professionals in understanding network architecture and identifying potential vulnerabilities.
- It can assess the quality of network services and identify areas where network performance may need improvement.
- Network administrators use traceroute to optimize routing by choosing the most efficient path for data transmission.
14. What Is a Response Code? List Them.
Explanation of the question
HTTP (Hypertext Transfer Protocol) response codes are three-digit numbers returned by web servers to indicate the status of a client’s request. The codes are grouped into 5 classes:
- 1xx (Informational): These codes indicate that the server received the request and is continuing to process it.
- 2xx (Successful): Codes in this class signify that the request was received, understood, and accepted. For example, a 200-status code means the request was successful.
- 3xx (Redirection): These codes indicate that the client needs to take additional action to complete the request. For instance, a 301-status code tells the client the resource has been permanently moved to a different URL.
- 4xx (Client Error): Client error codes signify that the request seems to contain bad syntax or cannot be fulfilled. A common example is the 404-status code, indicating that the requested resource was not found on the server.
- 5xx (Server Error): Server error codes indicate that the server failed to fulfill a valid request due to an issue on the server’s side. A 500-status code, for example, denotes a generic server error.
15. Explain Brute Force Attacks and the Ways to Prevent Them.
Explanation of the question
Brute force attacks are a type of cyberattack where an attacker tries to gain access to a system or an account by systematically trying all possible combinations of usernames and passwords until the correct one is found. These attacks are time-consuming but can be successful if weak or easily guessable credentials are used.
Prevention Measures
- Enforce the use of strong, complex passwords with a mix of upper and lower-case letters, numbers, and special characters.
- Implement account lockout mechanisms that temporarily lock an account after a certain number of failed login attempts.
- Encourage or require MFA for user accounts to provide an additional layer of security.
- Use CAPTCHA or similar technologies to prevent automated brute force attempts.
- Implement rate limiting on login attempts to prevent rapid and numerous login trials.
16. What Is the Difference Between Vulnerability Assessment (VA) and Penetration Testing (PT)?
Explanation of the question
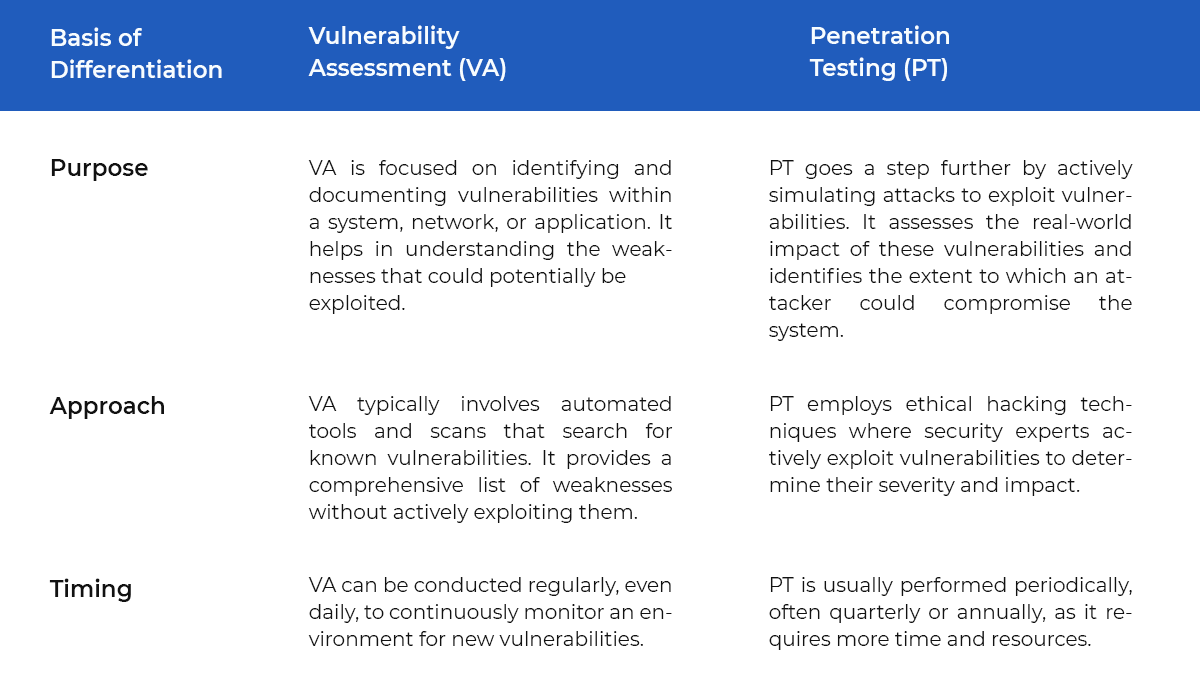
Practical Example
Let’s consider an e-commerce website as an example:
1. Vulnerability Assessment (VA)
The VA identifies that:
- The website’s server software is outdated and missing several security patches.
- It also detects that the SSL certificate is about to expire in a week.
- The assessment produces a report listing these vulnerabilities and advises the IT team to address them.
2. Penetration Testing (PT)
In a PT, ethical hackers actively attempt to exploit these vulnerabilities.
- They find that the outdated server software can be exploited to gain unauthorized access to the server.
- They also determine that the SSL certificate expiration issue can potentially lead to man-in-the-middle attacks.
- The PT report not only identifies these vulnerabilities but also illustrates how an attacker could compromise the system, potentially resulting in data breaches and financial losses.
17. When Should You Do Patch Management, and How Often?
Explanation of the question
Patch management is a critical aspect of maintaining the security and stability of your computer systems, networks, and software applications. Knowing when and how often to perform patch management is essential to protect your systems from vulnerabilities and ensure they run smoothly.
When to Do Patch Management
Patch management should be a routine and proactive process integrated into your organization’s cybersecurity strategy. You should perform patch management:
- Have a consistent schedule for patch management to ensure you don’t overlook important updates. This can be weekly, monthly, or quarterly, depending on your organization’s size and the criticality of the systems.
- Address critical and security patches as soon as they become available. These patches often fix vulnerabilities that cybercriminals can exploit. Delaying these updates increases your exposure to potential threats.
- Schedule patch management during planned maintenance windows to minimize disruptions to your daily operations. This can be during off-peak hours or weekends when system usage is low.
- Test patches in a controlled environment before deploying them to your production systems. Ensure that patches won’t introduce new issues or conflicts with your existing software and configurations.
How Often to Do Patch Management
The frequency of patch management depends on various factors, including the type of system, software, and the organization’s specific needs:
- Major operating systems like Windows, macOS, and Linux release regular security updates. These should be applied as soon as they’re available. Typically, monthly updates are common for operating systems.
- Software applications and tools used within your organization may have different release schedules. Check for updates and apply patches on a regular basis.
- These should be addressed as soon as possible, regardless of the regular schedule. Cyber threats can exploit vulnerabilities quickly, making immediate patching a priority.
- Older systems or applications may require special attention as they may not receive regular updates. In such cases, it’s essential to have compensating controls and security measures in place.
18. Explain the MITM Attack. How to Prevent It?
Explanation of the question
A MITM attack occurs when an attacker intercepts communication between two parties, such as a user and a website, without their knowledge. The attacker can eavesdrop on or modify the data exchanged. This is often done through techniques like ARP spoofing or public Wi-Fi interception.
Prevention Measures
- Implement end-to-end encryption using protocols like HTTPS (SSL/TLS) for web browsing, which makes it difficult for attackers to intercept and understand the data.
- Avoid using public Wi-Fi networks for sensitive transactions. If necessary, use a VPN (Virtual Private Network) to secure your connection.
- Enable two-factor authentication (2FA) whenever possible to ensure that even if data is intercepted, it cannot be easily misused.
19. Explain SQL Injection. How to Prevent It?
Explanation of the question
SQL injection is a common and dangerous web application vulnerability. It occurs when an attacker manipulates user-provided data to exploit vulnerabilities in an application’s SQL query construction. The attacker can gain unauthorized access to a database, extract, modify, or delete data, and even execute administrative tasks.
SQL injection is a type of cyberattack where malicious SQL queries are inserted into input fields on a website. If the website does not properly validate and sanitize the input, attackers can manipulate the database by executing unauthorized SQL commands.
Prevention Measures
- Use parameterized queries or prepared statements in your code to ensure that input data is treated as data, not as code.
- Validate and sanitize user input to filter out potentially malicious code.
- Limit the database user’s permissions to only those needed to perform specific tasks, reducing the potential damage from a successful attack.
- Deploy a WAF to monitor and filter incoming traffic to detect and block SQL injection attempts.
20. You Get an E-Card in Your Mail From a Friend. It Asks You to Download an Attachment to View the Card. What Will You Do? Justify Your Answer.
Explanation of the question
E-cards can be a fun and thoughtful way to send greetings, but cybersecurity is paramount. It’s crucial to exercise caution when receiving unsolicited emails with attachments, as phishing attempts and malware threats are prevalent. In such a scenario, I would exercise extreme caution and avoid downloading the attachment immediately.
Here’s justification for this decision:
Suspected Phishing
I will be cautious of e-card attachments, as it’s a common phishing tactic, often disguised as messages from friends but designed to steal data or plant malware.
Source Verification
To confirm the email’s legitimacy, I will directly contact my friend through an alternative communication channel like a phone call or separate email.
Email Scrutiny
Thoroughly examine the email, checking for sender anomalies and grammatical errors, as these can indicate a fake sender or phishing attempt.
Antivirus Scan
Ensure antivirus software is up-to-date and scan attachments for potential threats before opening them.
Unsolicited Attachment Caution
As a rule, you won’t open unsolicited attachments, even from known senders, I would remain cautious.
Download from Trusted Source
If the e-card is verified and safe, you will download attachment from the original source mentioned in the email, not directly from the email.
Be As Resilient As a Robust Firewall!
We’ve explored the top 20 cybersecurity interview questions and answers to help you prepare and demonstrate your knowledge and skills in the field. Armed with these answers, you’re better equipped to face the challenges of cybersecurity interviews, demonstrating your competence and enthusiasm for safeguarding the digital realm.
Remember, cybersecurity is not just about technical know-how; it’s about having a holistic understanding of the threats, the technologies, and the strategies to protect digital assets. Stay updated with the latest trends and practices, and always be ready to learn and adapt in this dynamic field.
Wishing you a future in cybersecurity that’s as secure as your codes!
