What approach to cybersecurity should your company take?
Cybersecurity is evolving into more of a business risk and no more just an IT risk. The proliferation of cyber-attacks is becoming a serious concern, considering the magnitude of damage it has caused in the recent years to companies, governments, and individuals.
What is cybersecurity?
In simple words, cybersecurity is the way of protecting oneself from hazardous and unauthorized entry by malicious intruders into restricted and highly confidential private data guarded by individual groups to protect them. In fact, ‘cybersecurity’ is a concept. There is no definite architecture or process or procedure to exercise it. It can comprise different combinations of technologies, processes, and controls that collectively aim to safeguard the system from cyber-attacks and unauthorized exploitation.
But, why cybersecurity?
When we learn to look at this entire idea from a higher perspective, we come to understand that cybersecurity addresses colossal concerns regarding data protection and prevent leakage. Highly sensitive data belonging to Governments, military, financial and medical fields of different nature and priority for a wide variety of purposes are kept safe by the practices of cybersecurity.
The portion of data, be it intellectual property, financial data, personal information or any other form of data when leaked or exposed due to infiltration is subject to bad consequences. As years roll, the potential damage that can be caused by cyber-attacks also multiplies and intensify. Areas like national security need utmost attention in the coming times and thereby the nation’s intelligence people get involved to mend the havoc and take the necessary action to ensure cyber-security.
Samples of cyber-attacks
One such example is the WannaCry attacks that happened last May 2017 which was notably the ‘biggest cyber assault in the history of times’. The ransomware incorporated itself into 3 lac+ computers and also into several other digital software across 150 countries.
So ultimately, the most obvious solution that we need to seek to guard ourselves is to adopt appropriate stringent measures. In the year 2014, Home Depot confessed that around 56 million cards for payment could be at a threat for a security breach.
Ways for effective cybersecurity
Classify data based on risk:
Each organization has voluminous chunks of data that contribute to its value and professional dexterity in the market. So as a first step, clearly categorize! Differentiate the ‘sensitive’ data from the not-so-important ones. Immediately after that, try to understand the bad impacts that could fall into place if the security of that data is compromised. This is popularly called as ‘proactive cyber risk management’ – forecasting the dangers and clearly building walls to ensure safety.
Develop a tailor-made strategy:
Now that you have identified and classified all the risks that are involved, devise a new plan to practice cyber-security in your business. So in order to strategize an effective cyber-risk immune program, you need to come up with an overall outline of the cost, risks, and benefits involved in the technologies and techniques you want to include as part of your program. Start investing in the right technologies in order to track and monitor the security breaches that spark off from the employee side from their individual systems.
Pick a data loss prevention system that is compatible with your business and a one which is easily configurable to your existing hardware. The second action item is to enhance the already existing firewalls and security measures you have already deployed. For instance, you can make changes in the existing configurations and tighten security in places where you find there are chances for possible data leakage. In the end, it is all about choosing the right software solutions for your business!
Bring in more awareness:
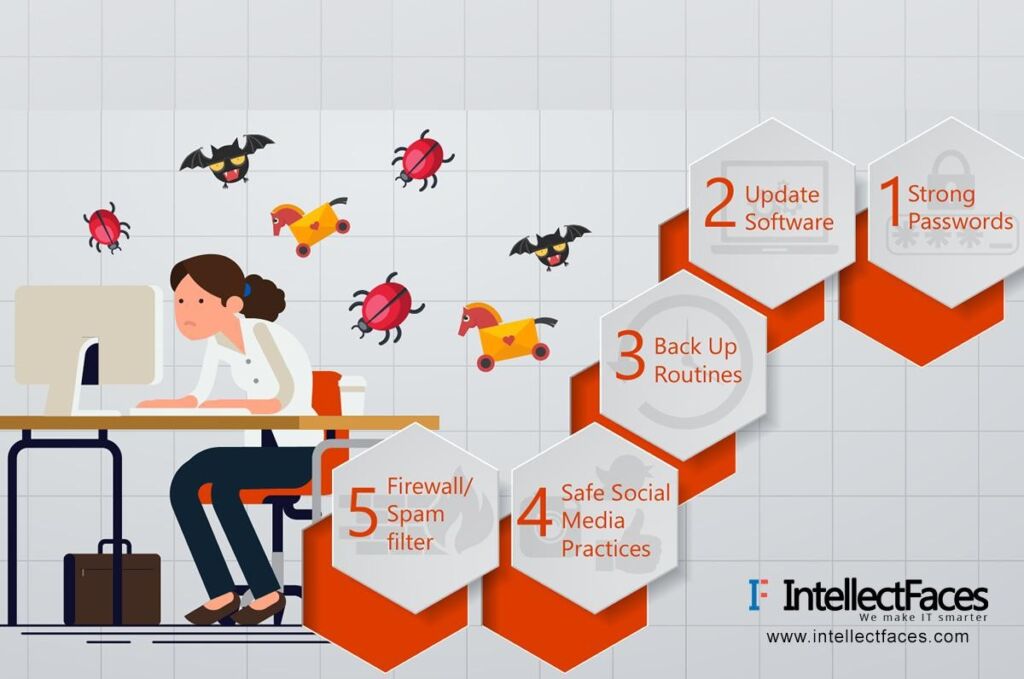
As a first move, educate all your employees by giving them sessions and lessons that impart the importance of cyber-security in them. Bring in stringent rules and introduce policies that bash offenders. Good internet practices cover most of the areas that can invite cyber-attacks. So make this known to all your employees. Draft clear do’s and don’ts that are expected of the employee from your side.
The most important step is to exercise a security-related incident to bring in more awareness. Also, it is a great way to keep all your peers and employees well prepared even before the onset of a security breach. Make it clear to the entire employee base that a unified, collective response from all levels is necessary to prevent a cyber-attack.
Alignment with best practices:
It is important to set the culture is such a way that the security policies of the company are clearly coupled with everyday activities. Also, set up the walls higher in terms of the legal papers so that any criminal entry into your private zone is strictly hindered. Stick up billboards in common places stressing the importance of adherence to company policies in terms of security. Bring in mandatory online courses, videos, and quizzes that teach the compliance practices to associates and test them as well.
Few best practices:
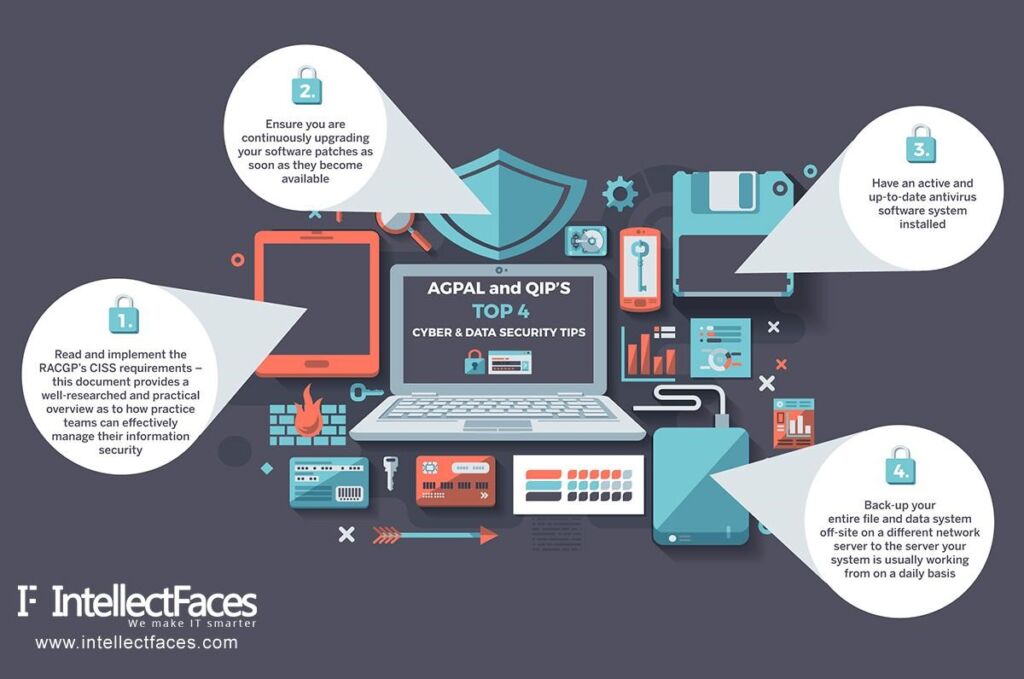
In terms of firewalls, virus alerts and data monitoring software, bring in all the technology you can afford within your planned budget and strongly equip yourself to deal with intrusion-prevention techniques. Set up a separate IT team to focus on the security of the most confidential data and preserve it with utmost attention from all aspects. Also, respect every security report instead of overlooking it.
Compartmentalize all your networks in such a way so that a breach into one area does not cause a chain reaction and make it easy for the intruder to get access into all other areas. Track as much online activity of your employees as possible and keep it under check. Always, always have multiple copies of your most valuable data and store them in different geographical locations such as hard drive, cloud storage, etc.